SSL is an integral part of today's web experience. Sites like Google penalize sites -- ANY sites -- that do NOT use SSL, so having a solid SSL implementation for any of your domains means your users will have safe and secure browsing experience. In addition, it eliminates that pesky "Safe Browsing" warning that Google displays for sites that don't utilize SSL and that tend to scare users.
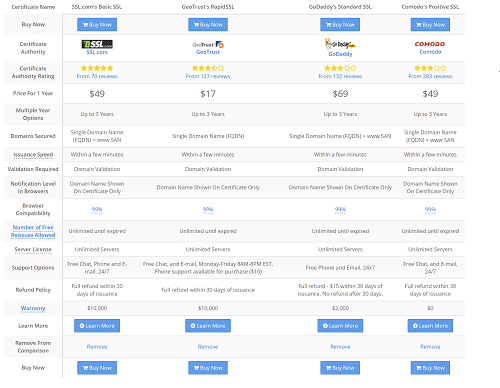
While implementing SSL is a wise move, it comes with a cost. A standard SSL certificate is relatively inexpensive, and if you use a site like SSL Shopper you can find single-use SSL certs for as low as $17/year. "Single-use" means that those inexpensive certificates are only good for a single domain. If you have multiple different domains to secure, or multiple second- and third-level domains like "support.yourdomain.com" or, for our purposes, "mail.yourdomain.com" you'll need a wildcard certificate for each top level domain (which secures anything.yourdomain.com) or possibly a UCC, which can be used to secure multiple single domains. These types of certs aren't so inexpensive.
That's where a service like Let's Encrypt comes into play. Let's Encrypt is a free, open and automated Certifying Authority. Unlike places such as GeoTrust or Trustwave, the SSL certificates issued by Let's Encrypt have zero cost. However, their certificates are just as secure and reliable as paid certs. The difference is that Let's Encrypt is like any open source product: while free, it may lack some of the nuance of paid services. That's to say that using a Let's Encrypt cert is slightly more work than using something from GeoTrust. For example, you have to "enroll" the certificate in the server's Certificate Store plus you have to handle automated renewals of the Let's Encrypt certificate. In addition, some options aren't available as of yet, such as wildcard certificates. However, the Let's Encrypt community is rapidly growing and they've announced wildcard support is on the horizon. Even with the limitations, the effort required for using Let's Encrypt is well worth it. Below we'll run through how we've implemented Let's Encrypt for our installation of SmarterMail and how we're handling both the enrollment of the cert AND the automated renewal.
While there's nothing built directly into SmarterMail to handle Let's Encrypt certificates and their enrollment, you can leverage one of their many Windows clients to handle this in a number of ways. One solution that we've found to be the easiest is to use the Certify client to handle the enrollment of the certificate. (This will also handle certificate renewal.) Once the certificate has been set up using this utility, you will need to automate the process of exporting the certificate into a PFX format containing the private key. (You'll need to do this since SmarterMail does not tap into the certificate store directly but instead references direct PFX and .CER files assigned to your ports.) This can be accomplished with PowerShell, and the script you need is below. Just be sure to modify the parameters of the script to match your environment. You can then set up a Scheduled Task within Windows to call this PowerShell script on a daily basis, and it will keep the certificate up-to-date. Finally, just secure your ports per our KB instructions and point it to the PFX file exported by the script.
The big caveat to this solution is that it's not free if you're securing more than one IIS site. So if you're only securing SmarterMail, it will work great. However, if you wanted to use this for your other websites as well, you would need to purchase the license for the Certify client or find another method, such as the ACME client. If you go with the ACME solution, it seems to be pretty straight forward and uses PowerShell modules, so this can be performed remotely as well. Here's their quickstart guide that walks you through their process, and also details how to export as PFX at the end of the article.
Using Certify and Let's Encrypt to secure SmarterMail's web interface and protocol ports
As mentioned, one solution for requesting Let's Encrypt certificates is to use the Certify client to handle the enrollment of the certificate as well as the automatic renewal. (Please note that the Certify client is only compatible with SmarterMail 16.x and the most recent release of SmarterMail 15.x.)
Configuring the Certify Client
Once certify has been installed on the server the instructions below will walk you through configuring the certificate automatically based on the IIS settings.
- Launch Certify.
- Select New Certificate in the upper left hand corner.
- The 'New Managed Certificate' section will then load.
- Select your 'SmarterMail' IIS site.
- Customize the Name if desired.
- Ensure the checkbox for 'Enable Auto Renewal' is enabled.
- Select the Primary Domain name for the desired domain.
- Select the desired Alternative Subject\Domain names to secure your secondary domains. Please note if you are not seeing the desired hostnames in this list, you will need to add an IIS binding for this hostname so that Certify can detect it.
- Click Save - At this point Certify should kick off the domain verification process. Once complete the site will be updated with the new SSL bindings and certificates within IIS.
Automating the certificate export from the Microsoft Certificate Store to secure SmarterMail's ports
SmarterMail requires a PFX or CER file to reference for the port configuration in order to secure the POP\IMAP\SMTP\XMPP ports for SSL\TLS communications. The Let's Encrypt certificate will need to be pulled from the certificate store every 90 days when the certificate reaches its expiration period.
Below is a PowerShell script that can be leveraged to export the desired certificate using into a password protected PFX file that can be referenced by the SmarterMail port configuration:
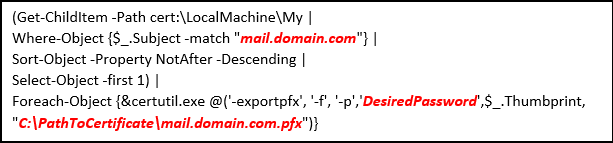
The script above contains three bold and italicized entries that will need to be adjusted to match your environment. You'll want to save this script after changing the variables. In our example, this was saved to C:\SmarterMail\Scripts\ExportCert.PS1.
Once this has been created you will then want to create a batch script to call on PowerShell to execute the ExportCert.PS1 script created above, the script you will want to leverage is below:

Save this as ExportCert.bat under C:\SmarterMail\Scripts.
Next create a Windows Scheduled Task that runs daily to execute the ExportCert.bat script. During the task creation ensure the option is set to run whether the user is logged on or not, and is also set to run with highest privileges to ensure the private key can be exported from the certificate store as expected.
Once this has been configured and run for the first time, you would need to configure the SmarterMail ports to use the newly exported certificate for SSL\TLS communications. Our KB article on configuring SSL\TLS contains the steps for configuring this under the 'Follow these steps to add a port to listen over SSL or TLS' section.
And there you have it! You're now using Let's Encrypt to secure your SmarterMail installation and can now avoid those pesky "Safe Browsing" warnings.